Friday, January 18, 2013
Wednesday, August 25, 2010
Why I Don't "Like" Mark Zuckerberg
 Whether you use Facebook to connect with friends and classmates across the country, or if you use Facebook to promote your business, we all know there are many intricate settings and restrictions on Facebook that can either help or harm our personal and professional brands. This is a story of one of those settings that isn’t helping any of us.
Whether you use Facebook to connect with friends and classmates across the country, or if you use Facebook to promote your business, we all know there are many intricate settings and restrictions on Facebook that can either help or harm our personal and professional brands. This is a story of one of those settings that isn’t helping any of us. · You are allowed to change the random character URL to a custom URL once.
· You are then only allowed to change your custom URL once again.
Fan Pages have even more restrictions on what can be modified.
1) Have the developers allow for multiple URL changes.
2) Have a customer service representative available to discuss the situation to see if it will allot for a URL modification.
Either way – Facebook needs to relinquish some control so that users can fully customize their pages. Why should we have to deal with invalid URLs that don’t represent us correctly?
|
Bookmark this post:
|
|
Thursday, August 19, 2010
The Importance of a Disaster Recovery Plan

What would it be like if your ecommerce organization’s website crashed for four days? Sounds horrifying right? Well, recently American Eagle® Outfitters experienced a system failure that lasted an unprecedented four days (followed by an additional four days of technical glitches)
An article from CIO Magazine recounted that American Eagle’s website went down when “atypical and concurrent failures [occurred] with IBM’s hosting servers and back up plans as well as with Oracle’s Data Guard utility program.” I’m not saying that websites don’t have their occasional hiccups, but four days is a massive detriment for a company whose ecommerce site is a large part of their business model.
The article quoted Brian Walker, a Forrester Research principal analyst urging other organizations to look at American Eagle as an example. “Get your responsibilities, processes and systems together now, test them, and correct as needed. Having a clear plan in and of itself will pay huge dividends in the event something happens.”
Senior Help Desk Associate at NSK Inc, Alex Straffin echoes the same sentiments. “Any type of Disaster Recovery plan needs to be tested in every way possible BEFORE the disaster actually occurs.” Many clients utilize NSK’s Backup and Disaster Recovery (BDR) solution that is managed by NSK. “We virtualize all of those clients’ servers off-hours for assurance as part of our ongoing BDR model,” says Straffin.
Straffin also notes:
DR plans are becoming more necessary as electronic business and ecommerce continue to expand. This is especially important if your site does not have any failover or redundant server configurations, and you are running high dollar, enterprise level ecommerce websites. A good DR plan will also include periodic verifications to assure that over time, your overall disaster recovery plan remains valid and ready to be put into action if needed.
The Bottom Line
As they say in the Scouts “Always Be Prepared.” Have a DR plan in place, that has been thoroughly tested, so should a disaster strike (knock on wood), you will know exactly what to do to reduce or eliminate downtime.
|
Bookmark this post:
|
|
Wednesday, August 11, 2010
The Importance of Antivirus
Malware On The Rise
Reuters recently published an article claiming that malware has hit an all time high. They state that McAfee, the number two security software provider, found that malware reached a new record in the first half of 2010. Malware is software code that, when introduced into a system, can hack the computer, steal passwords and identities, and reap havoc on system performance.
McAfee says that 10 million new pieces of malicious code have been catalogued. What is most noteworthy of these findings is that Mac systems are becoming increasingly vulnerable to attacks. Apple users tout that Macs are virtually “insusceptible to viruses,” however as Macs continue to increase their market share, their vulnerability is also rising.
Android Antivirus
In similar news, the first Trojan has been reported on the Android Operating System for smartphones. The malware poses as a media player and once installed on the phone, sends text messages to premium text numbers inadvertently charging the user. Hackers are usually on the receiving end of the text messages, and thus profit from the rouge SMS messages.
According to the article, posted on Mashable.com, Kaspersky Labs is in the process of developing a mobile antivirus application for Android phones, due to be released next year.
The Bottom Line
You need to take precautions. Whether you are dealing with your personal computer or your organization’s infrastructure, steps need to be made to make sure your system(s) are secured.
Basic necessities include using a firewall, password protecting your WiFi, and having an up to date antivirus system installed (including Mac systems).
Additional steps, such as security assessments and security audits can be performed to make sure your organization isn’t vulnerable to outside attacks.
Most importantly, self monitoring is the key. Be sure to stay away from sketchy websites (including those not suitable for the workplace) and making sure you only download files from people or websites you know and trust.
|
Bookmark this post:
|
|
Friday, July 23, 2010
Legal Advice For IT Professionals
Even though it may be your job to handle sensitive information, how you handle the data is just as important as how well it is secured.
One of the best ways to avoid any sort of legal snafu is to have a privacy policy in place. The policy needs to be all encompassing, meaning it covers EVERYTHING accessed on the company’s network (i.e. email, network drives, Twitter, Facebook, VPN connections from offsite, etc).
The policy should mandate guidelines of acceptable computer usage while using company resources (including all data).
Another step would be to conduct a Security Assessment and Security Audit.
- A Security Assessment identifies vulnerabilities within an organization’s infrastructure and will then recommend solutions to secure the system.
- A Security Audit installs an application on the network that is designed to identify, classify, secure, monitor and report on sensitive data. A manager is then notified every time the data is accessed so organization’s can track who is accessing sensitive data and when and where the access happens.
If you aren’t sure of your organization’s policy in regards to sensitive data, ask them. If they don’t have a policy in place – inquire about initiating one. This will help to safeguard yourself as well as the data you are in charge of.
|
Bookmark this post:
|
|
Friday, June 25, 2010
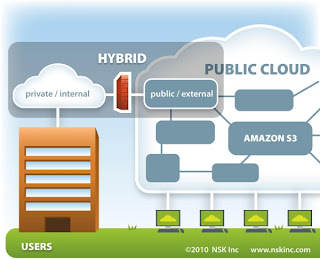
Public or Private Cloud?
IT Wants Them Both!
InfoWorld just published an article about a recent survey conducted by the International Data Corporation (IDC). In the survey, IDC asked IT executives if they preferred Private Clouds in comparison to Public Clouds. The results showed that many companies expect to use a combination of both Public and Private Cloud services. The mixed use of Public and Private Clouds is also referred to as a Hybrid Cloud.
With a Hybrid Cloud, an organization has their own private (internal Cloud) with services running within their firewall. However, Hybrid Clouds allow users to access data that is stored off site via a Public Cloud.
This model is beneficial when an organization wants to have control over their data storage, but needs additional space for archiving data. They have the security and supervision of the Private Cloud in their network, but can store excess data in a scalable on-demand Public Cloud.
According to Frank Gens, an IDC chief analyst, “Virtually every customer, at least from the midmarket up, will have a mix of both [Public and Private Clouds].”
Additional information about Public, Private, and Hybrid Clouds will be available next week in the whitepaper “Hybrid Clouds: The Best of Both Worlds.”
|
Bookmark this post:
|
|
Wednesday, June 16, 2010
Is The Internet Running Out?
There has been a lot of buzz from people stating we are reaching the end of the internet's capacity. To be honest, all I ever can think of is the episode of South Park where internet access starts to dry up. In the episode, the "internet" is actually a giant Linksys router and Kyle reestablishes the internet by resetting the device. Although hilarious, the probability of the internet disappearing is pretty low (notice how I didn't say impossible).
Fiction aside, the internet is in essence a network of networks that connects computers and other devices across the globe. The internet isn't one specific device but rather a combination of billions of components. Despite its seemingly endless coverage area, a recent article from CNN.com reported that the internet may be reaching its user limits. Soon we may not be able to add more devices to the current configuration.
Here's the kicker; it all has to do with the internet's current configuration. Right now the internet runs on what is called Internet Protocol Addressing Scheme version 4 (IPv4). Within this particular set up - IPv4 only provides slightly more than four billion IP addresses because it is based on a 32-bit format. These addresses are usually represented with decimal points separating the address into four parts (i.e. 192.0.0.000).
IPv4 operates on two basic functions: addressing and fragmentation. The protocol uses the IP addresses to transmit internet datagrams to their destinations (also known as routing). Then these datagrams are fragmented and then reassembled once they reach the destination address. (More information on IPv4 operations can be found in the IETF Publication RFC 791).
Anything hosted on an IP network (computer, printer, smart phone, etc.) is assigned its own unique IP address. Thanks to advancements in technology, ownership of mobile phones, net books, Ipads, and other web enabled devices has exploded. These new devices are gobbling up IP addresses at an alarming rate.
I spoke with Senior QA Associate Apollo Catlin, at NSK Inc, and he mentioned that a smart phone itself "probably has three different IP addresses associated with it." Numerous reports have speculated that within the next two years, we will run out of IP addresses. According to Catlin, when IPv4 was first instated in the 1970's there wasn't any thought of running out of addresses as "they didn't ever think people would have a personal IP address." Back then, IPs were reserved for mainframe computers used by large organizations not individuals.
So What Can Be Done?
The most viable option is to transition from the current IPv4 configuration to IPv6. IPv6 operates on a 128-bit system meaning there are trillions of new IP addresses available under this protocol.
Unfortunately content providers are reluctant to transition to the IPv6 protocol. Catlin states that the transition would require a complete overhaul of the Internet infrastructure in that the "entire middle structure of the system needs to be replaced."
Although tedious, this transition needs to happen soon. Otherwise in a couple of years, internet access may only be available to current users as we may not have any new IP addresses to hand out. The internet is open to everyone; let's not start having to ration it out.
|
Bookmark this post:
|
|